PrivacyPortfolio's Vendor Risk Management Platform
This is my homemade Vendor Risk Management Platform.
As you can see, I have an inventory of all my vendors, which I maintain as a dataset in my data catalog.
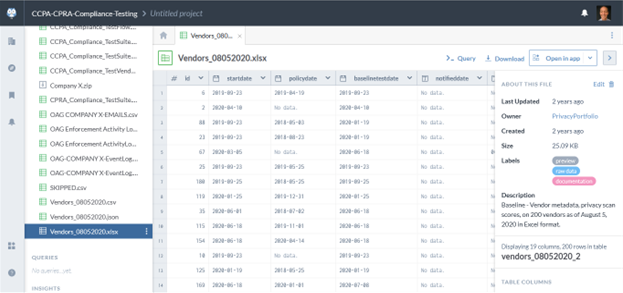
It’s open to the public, but each vendor is de-identified and other identifying details are redacted.
This platform offers the ability to share and correlate datasets with researchers, vendors, enforcement agencies dynamically in real-time or for static point-in-time. For each vendor, I have a folder for storing all my agreements, assessments, and evidence. Each folder is encrypted and stored inside a tagged container within a data pod store for all my vendors. On my laptop, these folders look like ‘regular folders’:
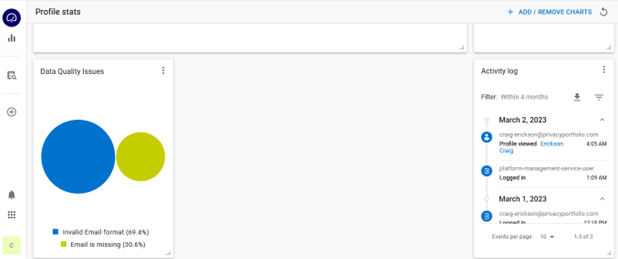
In addition to using data.world as my data catalog, and Inrupt SolidPods as my secure data store, I also use Reltio Identity 360, a master data management tool that calculates the quality of data I collect.
Any code or other tools I use for collecting, processing, protecting, accessing, or sharing any of this information are maintained in my public or private Github repositories.
Craig Erickson's Vendor Risk Management Program
My Vendor Risk Platform
has no utility or value without my Vendor Risk Management Program.
My Vendor Risk Program
defines and classifies who is a vendor, how the vendor and their
resources will be evaluated,
and guides which actions I
can take to reduce my risk exposure.
“Know Thy Vendor” is the first principle of my Vendor Risk Program.
If my vendor obfuscates who
owns the business or brand, where they are located, or how to contact
them,
I can't identify who I'm
sharing my personal information with, or how it's being used.
“Vendor Communications” is the second principle of my Vendor Risk Program.
A vendor who can’t or won’t
communicate is a very big risk.
Vendors often protect
themselves by restricting communications through third party service
desks,
unattended email aliases,
and third party email and messaging systems.
“Vendor Value” is the third principle of my Vendor Risk Program.
If what the vendor offers
doesn’t provide adequate value to me, I can't afford to manage that
relationship.
Value is a risk factor. Cost
is a risk factor.
It can take time to verify
that a product or service works as advertised,
and evaluate whether it's my
usage or the vendor's performance that needs improvement.
That’s why I onboard vendors
first and vet them later. I'll either terminate the relationship
or take other measures to
reduce any risks -- after I find out what those risks are.
Vendor Risk Management is NOT synonymous with Third Party Risk Management.
My relationship to my
vendors are first-party relationships and personal information I
voluntarily share with my vendor is first-party data.
My third-party relationships
are with my vendors’ vendors and personal information my vendors share
with their vendors is third-party data.
Organizations that sell personal information to my vendors are also third parties,
which includes data brokers and other sources of consumer profiling.
Vendor Risk Assessments
If there is a risk of
physical, emotional, social, or financial loss due to a vendor,
I need to assess that risk
and handle any issues.
Consumers and businesses
both have legal and financial mechanisms to reduce these risks and in
some cases,
compensate for losses, but
this too, takes effort on my part to maintain my own financial leverage
or legal standing.
For example, if a vendor
responds “Yes” they have both MFA and SSO available to protect access to
my account, but I decline to use it,
my risk is greater. I never
ask them, “What’s the risk of using your product or service if I ignore
all your recommended best practices?”
When I manage vendor risk on behalf of a business, I’m concerned about:
- How I’m going to provision the offering and delegate access to users
- How I’m going to patch the offering or report issues to receive support
- How I’m going to train users on best practices
- How I’m going to remove or replace the vendor’s offering if necessary
In essence, to reduce my risk exposure, I first make sure the offering suits my requirements, and then make sure I’m using the asset in accordance with the vendor’s recommendations.
Data Quality as a Risk Factor
Shipping my order by mistake
to someone else’s house, or erroneously sending my bank statement to
someone else’s inbox
is a risk of doing business
that I've come to accept.
It's just a flaw - an issue
like any other issue, which may or may not be resolved.
Issues may be caused by
logic or process flaws, which are difficult to determine from the
outside.
Issues could also occur as
the result of poor data quality. And poor data quality can be due to the
consumer voluntarily submitting data,
the business processing the
data, or the entity who sells, purchases, or steals data.
Collecting data from
multiple sources can improve data quality by correlating and verifying
the data.
"It depends" -- validating
residential addresses with the USPS, for example,
is considered by most
businesses to be more accurate than the address provided by the
consumer,
and typically overwrites the
consumer-provided address.
Digital identities are more
challenging,
and as the pool of data
sources increase, data quality can increase or decrease –
and this often depends on
accessibility of data sources. Searching someone on Google free of
charge
yields very different
information than paid subscribers to CLEAR, a service from Thomson
Reuters.
Availability is also an
issue:
Verifying a person’s
identity is unreliable when the consumer or the business relies on
technology
vulnerable to service
disruptions.
Reference data should be
durable or relatively stable, at the least.
If not owned or governed by a
generally-accepted standard like International Time Zones,
everyone is free to choose
their own source of reference data, or they can create their own
self-sourced reference data.
Classifying individuals and
organizations into groups is a generic activity for managing risk.
If I want to protect myself
from registered sex offenders, I’ll need a list. But whose list?
Anyone can post a list.
Whether the list is about Deadbeat Tenants who don't pay rent,
or Deadbeat Data Brokers who
didn't pay their registration fee,
the quality of data matters
because it impacts what decisions are made
or action taken by the
person relying on that data.
Using Master Data Management to score Data Quality of Personal Profiles
As you can see, I have a
tool called Reltio Identity 360,
which allows me to compose
and maintain consumer profiles shared with specific vendors
and third parties who sell
my personal information.
By measuring the cumulative
quality of data associated with each consumer profile collected by my
vendors,
I can tag and track specific
datasets because I also master and govern my own personal information.
“Know Thy Vendor”, or
“Know Thy Customer”, or “Know Thy Enemy” are all first principles of
Vendor Risk,
and all center on
identity – which has no one single authoritative source of truth.
Who decides what my name is, how it’s spelled, or even how it's pronounced?
If it's not me, then who or which authority establishes my legal identity?
How does a consumer prove who they are?
I chose my US passport and
my photo on LinkedIn to be my two authoritative sources of my digital
identity
for verification purposes,
which has been notarized at my financial institution and posted on a
website domain I control.
According to the California
Privacy Protection Agency, this form of identification is not necessary
for consumers who
submit verifiable requests
to exercise their privacy rights.
But none of my vendors,
including my bank where my identity proof was notarized, accept my
proof.
Without digital identity
standards for authoritative documents and reliable mechanisms to
transport them,
everyone has their own
process, perhaps consulting their own reference data.
Some businesses use credit
cardholder data to verify the age of minors, while others use public
information,
like the US Census; or
private information, such as Melissa Data.
On the other hand, identifying my vendor is much more challenging –
I have even fewer tools and resources as a consumer,
and this step competes and interferes with the desire for immediate fulfillment.
When I install a mobile app,
visit a website, click on an advertisement, agree to accept all
cookies,
or perform simple tasks like
scheduling a meeting, signing electronic documents, or verifying my
email address,
I can’t verify who I’m
interacting with.
Is it a legitimate corporate entity or just some guy who runs a website,
or a bot behind a proxy that exists only for the moment?
Should I accept a third-party privacy policy?
Is it safe to download resources from another domain during the install process?
Entity resolution and
identity-proofing are essential techniques in managing vendor risk.
Phishing and malware attacks
cannot be mitigated by telling people to avoid clicking on a link from
an untrusted sender --
because that's the normal
business practice today.
How does your organization
provision its users to a new application?
Chances are, they are
invited through a vendor's third-party-hosted email system
via a donotreply email alias
that identifies neither the vendor, the resource, or the authorized
purchaser.
The California Consumer
Privacy Act (CCPA) is an essential tool for consumers managing Vendor
Risk
As a California Consumer,
exercising my privacy rights under the CCPA is like having an insurance
policy
against the unauthorized use
of my personal information.
I can seek redress from a
problematic vendor, after I “sign up”.
But I can’t return a
purchased item without a receipt,
or report that my product or
service wasn't delivered if there’s no return address or agent to
assist me.
I could turn to an agency
that enforces laws and governs business practices, as a form of
insurance.
But to file a claim, I needs
a legally enforceable policy,
proof in order to collect on
the claim,
and often I'll need an agent
to represent me who can assist me and possibly exert more influence
over the vendor than I could.
To make sure my claim is processed, I need to know:
- The corporate name as registered with the Secretary of the State the entity was formed;
- Nonbusiness entity
- Annual revenue;
- How many consumers’ personal information is sold or shared;
- Which “Categories of third parties” are with whom the business shares personal information.
- How the business verifies my personal identity.
My Vendor Risk Platform
is an essential tool for managing and testing my privacy rights
under the California
Consumer Privacy Act (CCPA)
I might have a legal right,
doesn't that guarantee I have 'legal standing' to pursue redress for
violations of my right,
nor the capability to do so.
My Vendor Risk Platform
provides the tools, the processes, the evidence, and the guidance
to ensure that I comply with my obligations as a consumer under the CCPA.
There are many exemptions,
exceptions, and other legal 'loopholes' which can be used to deny me
a fair opportunity to
present the evidence I have collected in support of my claim.
Only by testing the CCPA can
my Vendor Risk Platform identify vendors I consider risky because they
are 'uninsured';
i.e. businesses that are
either not covered by the CCPA,
or illegal business
activities which are not enforced by the appropriate agency.
My Vendor Risk Management
Program and Platform are real tools I use to manage my vendors.
How effective these tools are in protecting my personal data is for now, experimental.
I can only hope that this experiment will be educational for all participants and observers.
As a followup to this article, I will be offering a hands-on lab that uses my Vendor Risk Platform to process personal information under the CCPA. This learning lab is designed to help people reach specific objectives within a specific role-context. For example:
- "I am a Developer, and I want to protect sensitive personal information from being improperly shared"
- "I am a Product and Marketing Director who wants to avoid unnecessary requirements that could cause additional expense and delays in our product launch"
- "I am a Consumer who wants to know if my vendor is a high-risk CCPA-covered entity."
- "I am a third-party privacy consultant providing privacy-preserving products, services, and advice to businesses, and my clients need to know if our firm's solutions comply with the CCPA."
- "I am an enforcement agency investigating a complaint regarding a business' privacy and security practices, and I want to discover similar violations with other relevant laws"
- "I am a data broker registered with the State of California who wants to assess if my security and privacy risk controls support CCPA-compliant business practices"
- "I am a vendor risk manager, and I want to know if my suppliers are violating the contract terms required by the CCPA."
- "I am a third-party auditor who wants to know how many CCPA requirements are met using existing NIST controls."
- "I am an authorized agent for consumers who want to report CCPA violations in complaints or incident reports to appropriate enforcement agencies."
Please send me an email
if you'd like to participate in these learning labs when they are available.
Sincerely,
Craig Erickson, a California Consumer
Published 04/04/2023


